- May 23, 2023
- Jim
- 0
Educating the educators: cyber security for teachers
The Department for Science, Innovation and Technology (DSIT – a recent amalgamation of parts of DCMS and BEIS) has just released its seventh Cyber Security Breaches Survey: an annual data gathering exercise across businesses and charities on their approach to cyber security. In the final of our series of blogs reflecting on its findings, we consider the specific risks faced by the education sector, and reflect on how schools and colleges can help train their staff to respond.
The education sector is at greater risk of cyber attacks compared to businesses…
One of the most interesting facets of DSIT’s 2023 Cyber Security Breaches Survey has been its dedicated annex considering cyber security in the education sector. The statistics are illuminating: in the past year 50% of higher education institutions and c.30% of further education colleges reported experiencing an attack or breach at least weekly (compared to about 21% of businesses). Even in schools, the figure is 15% and 20% for primary schools and secondary schools respectively – a figure that would have seemed preposterous only a decade ago.
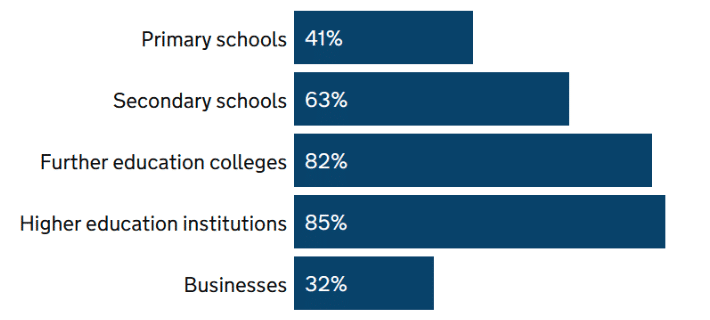
Figure 1: Percentage of organisations that have identified breaches or attacks in the last 12 months (source: DSIT Cyber Breaches Survey 2023)
These attacks included a wide range of methodologies, including impersonation, malware and denial of service attacks; and they were successful too: 61% of high education institutions had a negative outcome from a cyber attack in the past year: 45% of which included account compromise for illicit purposes. Two recent examples highlighted by Education Business include Hardenhuish School in Chippenham, subject to a ransomware attack on their IT systems, and Pates Grammar School in Gloucester, which saw students’ and parents’ passport scans and teachers salary and contract information leaked online. Compare this to large businesses, of which only 8% reported account compromises.
Education establishments provide an attractive target for a whole range of malicious actors. Universities conduct groundbreaking research and develop sensitive technologies that can provide valuable commercial or national security advantages to the attacker who can steal it. Meanwhile, younger children are ideal targets for synthetic identity theft and impersonation, and it may be years before the victim even realises they have been compromised: perhaps at the point where they apply for a credit card or seek to buy a house, only to find that an invisible attacker has ruined their credit score.
…but is doing a decent job of tackling the problem
The good news is that the education sector appears to recognise its vulnerability and is taking action to prioritise it. DSIT found that almost all educational institutions (whether primary, secondary, colleges or universities) reported cyber security as a high priority for their governors or senior managers, with specific responsibilities assigned to seniors in the majority of institutions (ranging from 61% of secondary schools to 87% of universities). The survey also found that the sector was doing a good job in implementing controls, especially around supply chain assurance and basic technical solutions such as patching and firewalls, as figure 2 demonstrates.
One of the areas that educational institutions did report challenges with however, was, somewhat ironically, in training their staff. Identified blockers to effective training included lack of time and resources to run or attend training (especially during term time), but also a lack of interest from staff in the issues. Training exercises or incident simulations were seen as particularly difficult to run given the potential disruption to students. As a result, only about half of schools have undertaken any staff cyber security training or awareness-raising activities in the past year, though the figure rises to more than eight in ten of colleges and universities, and all types of educational institutions are better than the average business (only 15% of which have conducted training in the past 12 months).
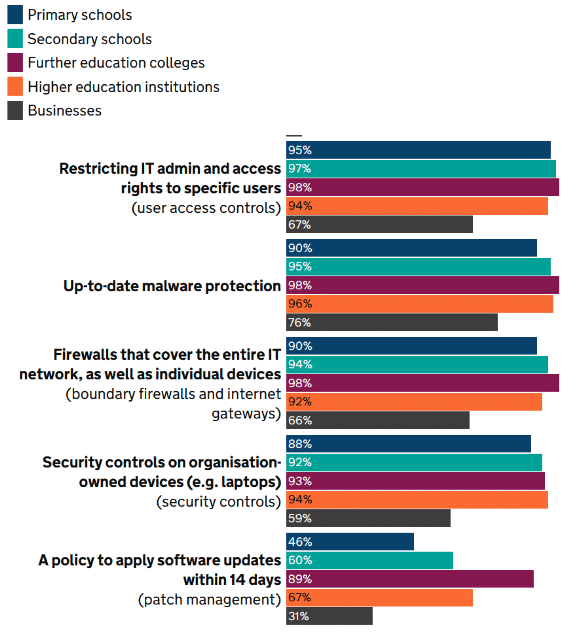
Figure 2: Percentage of organisations that have the rules or controls in place in the five Cyber Essentials technical areas (Source: DSIT Cyber Breaches Survey 2023)

Educating the educators: short, relevant and actionable
Given the specific training challenges facing teachers and educational staff however, bespoke support may be in order. Principle Defence’s experience indicates that, in most schools, whilst there may be a person with responsibility for cyber security or data protection, this is usually a task on top of the person’s (often unrelated) day job – and one that they may have grudgingly been ‘volun-told’ for. More generally, teachers have a crucial role to play in protecting personal data, but often work incredibly long hours and may have neither the technical expertise nor the capacity to become security experts (on top of their safeguarding, Prevent, and other multitudinous non-teaching responsibilities…)
With this in mind, we suggest abandoning generic Cyber Security 101 training packages to focus on the practical and tangible actions institutions need their staff to take – whether that’s strengthening their passwords, reporting phishing emails, or encrypting emails containing personal information.
Likewise, tailoring the content to the context is crucial to maintain engagement and ensure the risks feel relevant to staff. Teachers, as you would expect, care deeply about the welfare of their pupils: focusing on the potential impacts on students of a successful cyber attack is more likely to motivate behaviour change than a recitation of the dry legal risks to the academy trust. Meanwhile, creating function-specific training tailored to the individual roles and responsibilities of teachers, administrative staff or governors can ground both the risks and the suggested response in a realistic scenario.
As well as targeting the content, educational institutions should focus on the format and logistics of the training. This can be as simple as providing some time for participants to take requested actions immediately afterwards. One teacher told us that every year her school’s cyber security training encouraged her to strengthen her password. But the minute the training ended, she was swept back into the chaos of the school day; password changing postponed ‘until she had a suitable moment’, and in most cases, inevitably, forgotten about.
Keeping sessions short – with time for discussion afterwards – was felt by DSIT survey participants to be effective, and we’d add that repeating them throughout the year can also increase their positive impact. That doesn’t mean a dull ten-minute powerpoint presentation at every inset day however. Consider gamification, quizzes, and case studies, or seek the permission of the governors to conduct some open-source research on them and demonstrate the (often unwitting) extent of their online presence. After all, schools, colleges and universities are experts at encouraging their students to learn in all manner of innovative and varied ways. They should look to utilise the same techniques and strategies on their own staff.
Principle Defence is a certified cyber security and data privacy training provider and can support your school or college’s training needs: all the way from awareness-raising packages to professional certifications for responsible staff members. Please do contact us to find out how we can help your organisation build its staff knowledge and awareness.