- May 1, 2023
- Jim
- 0
Planning for the worst: the value of pessimism
The Department for Science, Innovation and Technology (DSIT – a recent amalgamation of parts of DCMS and BEIS) has just released its seventh Cyber Security Breaches Survey: an annual data gathering exercise across businesses and charities on their approach to cyber security. In the second of a series of blogs reflecting on its findings, we consider the low numbers of businesses with incident response plans in place, and discuss some practical tips for preparing for a cyber attack.
One of the most stark findings of the 2023 Cyber Security Breaches Survey was the disconnect between the number of cyber incidents, and the number of organisations that plan for them. About a third of businesses and a quarter of charities report having experienced a cyber attack in the last year, rising to 69% of large businesses. Of those, 40% experienced a breach or attack once a month, with a fifth reporting an attempt at least once a week. Yet, the data indicates that only 21% of businesses and 16% of charities have an incident response plan to deal with such an attack.
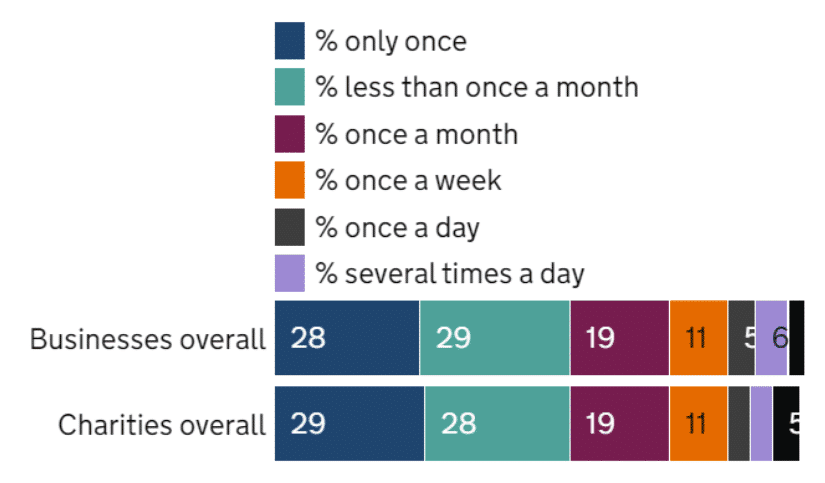
Figure 1: How often organisations have reported breaches or attacks in the last 12 months (source: DSIT 2023 Cyber Security Breaches Survey)
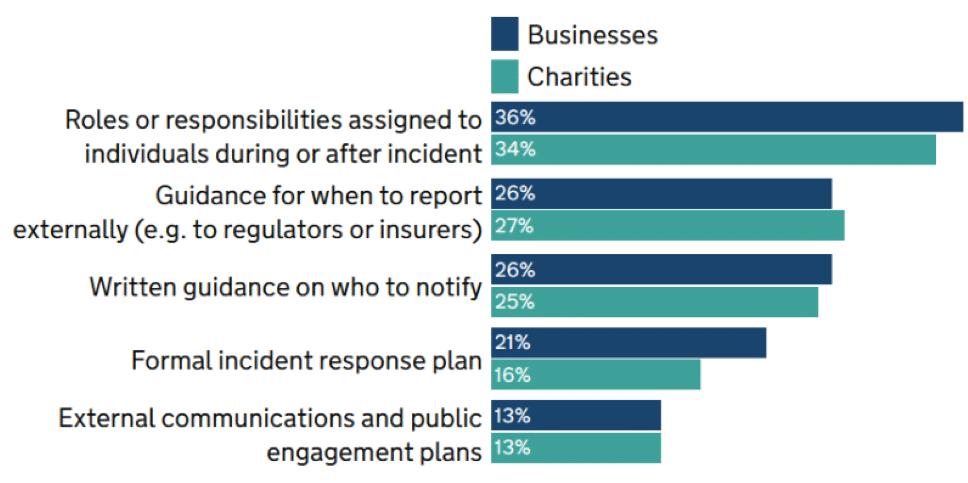
Figure 2: Percentage of organisations that have the following measures in place for dealing with cyber security incidents (source: DSIT 2023 Cyber Security Breaches Survey)
This headline figure does of course generalise across all types and sizes of business, but even when you consider the data for large businesses and high-income charities only, the results are still worrying: 64% and 38% respectively. Moreover, under half of large businesses had a communications plan in place, despite the possibility of an attack causing large scale service disruption, media attention, and reputational damage.
Do these figures represent a continued desire by organisations to stick their head in the sand and hope the worst will never happen? The qualitative evidence from the survey suggests the answer is more complicated than that, with planning hampered by a combination of a lack of expertise, a disconnect between IT teams and senior management, and overall just a sense of the futility of planning for unpredictable events.
With this in mind, we offer five tips to support pragmatic incident planning within your organisation:
Five tips for pragmatic planning
- Plan for outcomes, not scenarios
Cyber attacks can come in many different forms, and writing a bespoke plan for each variation of virus is burdensome (and, moreover, would most likely confuse the actual response, especially when the attack’s cause might not always be immediately known). However, planning for outcomes is more predictable and will enable your organisation to adapt and respond to multiple sorts of attacks: now and in the future. Map out what impacts a successful attack could have on your organisation (e.g. service disruption, loss of personal data, loss of corporate functions) and plan for these, rather than every potential eventuality. You’ll find your incident response plan(s) can be much clearer and more streamlined as a result.
Bring others in
A successful cyber attack doesn’t just affect IT teams, but will have ramifications for functions and operations across the entire business. Your incident plan needs to take account of how the organisation will deal with HR, legal, financial and customer-facing impacts as well as the technical resolution of the issue itself. Likewise many decisions ‘on the day’ may need to be taken by responsible functional leads. Running an informal table-top exercise to dig through the possible implications of an attack across the business can not only help you understand what to expect, but also provide a helpful means of raising awareness and upskilling your colleagues of what they may need to do in the event of an attack.
Practice makes perfect
One of the hardest parts about incident response planning is, counterintuitively, when the incident never ends up happening. Plans are forgotten, people move on, and circumstances (corporate structures, responsibilities and clients) change. Under these circumstances, complacency and skill-fade easily set in. Counter this by planning out an annual programme of training, exercises and drills that keeps knowledge fresh and maintains interest. Not only will it enable you to keep your people prepared and ready, but it should allow you to ensure your plans remain up-to-date as well.
To avoid any risk of overburdening people, keep the roles, processes and accountabilities as similar as possible from exercise to exercise, whilst keeping the scenarios fresh and interesting. This will help participants to practise their roles and improve their skills with each iteration, whilst ensuring each exercise brings fresh interest and learning.
Incident response vs business continuity
In addition to your incident response procedures, which will focus on the steps needed to respond to an attack, you should also consider creating an additional Business Continuity or Disaster Recovery plan. This specifically considers how your organisation will recover from an attack, and/or how its most essential functions will be maintained in the meantime. These plans and procedures are especially important in the wake of a disruptive attack which may cripple your usual service delivery or permanently remove your access to particular systems.
Disaster recovery plans should consider issues like key business operations that must be kept running, the priority order for recovering services, and the creation of a ‘Minimum Viable Company’. It could answer questions such as where you would procure essential equipment at short notice, how you would recover your information, and how you would continue providing services to customers in the meantime.
Communication, communication, communication
As the survey showed, even amongst businesses that have formal incident response plans, the numbers with an associated communications plan are really low – just 15%. But in a world where a successful cyber attack can bring down your business or ruin your reputation, it is increasingly naive to hope that incidents can be kept under the radar from your customers. Prepping your key messages in advance and ensuring your PR team is bought into your public communications strategy will avoid mixed messages or embarrassing delays in the event.
Even if the disruption is confined to internal operations, you will need to have a plan to communicate with your employees as to what action they should take (or shouldn’t take!). When developing your internal and external communications strategy, consider that, in some worst-case scenarios, you and/or your employees may not have access to normal channels of communication, and consider alternative information routes such as phone trees or mobile alerting systems.
Don’t let your first successful cyber attack come as a surprise – accept that, even with the best controls in the world, you are always vulnerable, and prepare accordingly.
Principle Defence can support your organisation to consider its incident response plans, including running exercises for a range of scales and scenarios. Our free ‘Cybersecurity Key Terms and Concepts’ e-book also has some helpful primers on disaster recovery, response procedures and exercising for those starting on their incident planning journey. Get in touch if you’d like to know more.